ExifTool is a forensic tool, which is installed on Backtrack 5 R3 and can be used to extract metadata from different files, so you could say nge forensic digital data.
For more details, we immediately wrote to its use.
—Start Exiftool
—Glide to the directory
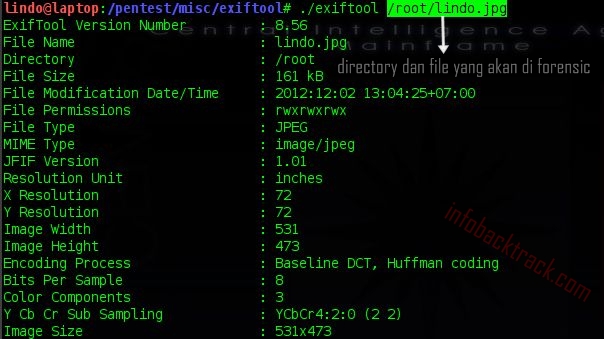
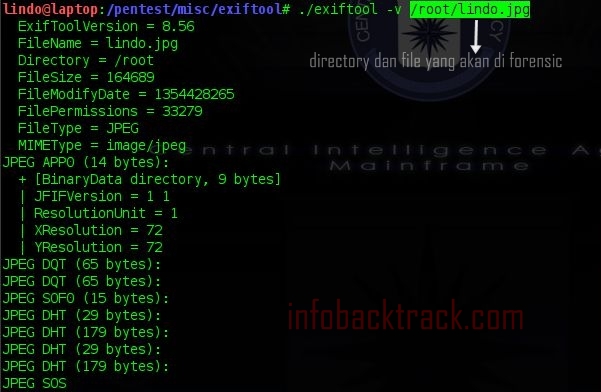
Okay we immediately try to test for a forensic image file. Here I use the pictures 'lindo.jpg', and the results can be seen from the screen shot below.
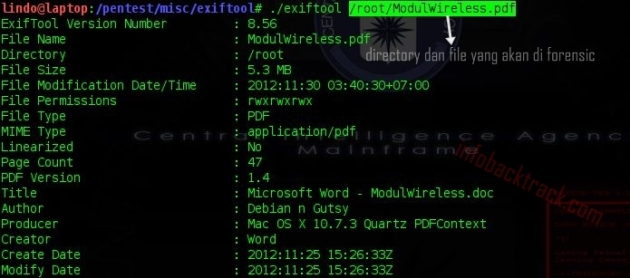
Next we test a forensic * PFD. This time I will try artificial forensic ModulWireless.pdf made by Mr. Hero .
—Verbose Mode.
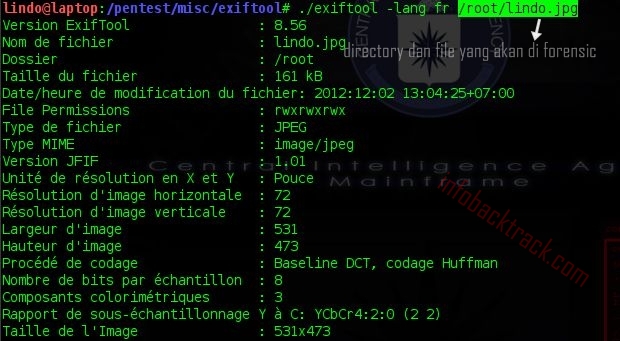
—ExifTool also supports multiple languages, eg languages francis (fr).LOL
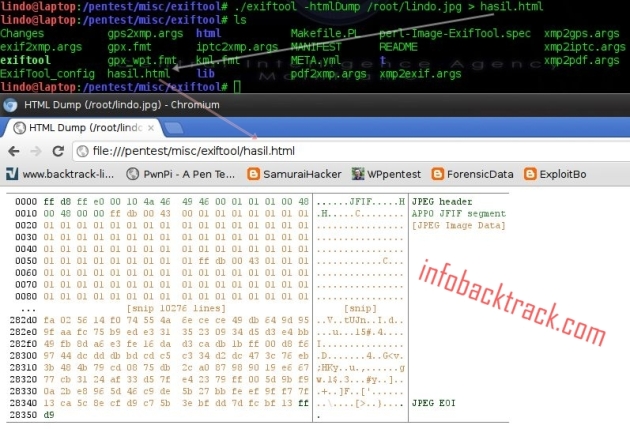
—Generate html format binary dump.